8 Key Protocols You Can’t Ignore, 5 Steps to Understand How VPN Tunneling Works, and 7 Smart Strategies to Reduce Latency – Sketech #18
3 bold, high-energy visuals and insights to help you understand, apply and remember technical ideas instantly
Hey! Welcome to Sketech 18 Free Edition, where complex networking concepts become clear, visual, and easy to grasp.
Last week’s edition sparked great discussions, love seeing how these visuals help make learning stick! This time, we’re diving into critical networking topics that every engineer should master:
8 Network Protocols Explained in a Simple Way → From HTTP to SSH, understand how these core protocols enable seamless connectivity and secure communication.
5 Steps to Understand How VPN Tunneling Works → A step-by-step breakdown of how VPNs encrypt and reroute your data.
7 Smart Strategies to Reduce Latency → Proven techniques to cut delays, optimize data flow, and boost system performance.
Let’s dive in!
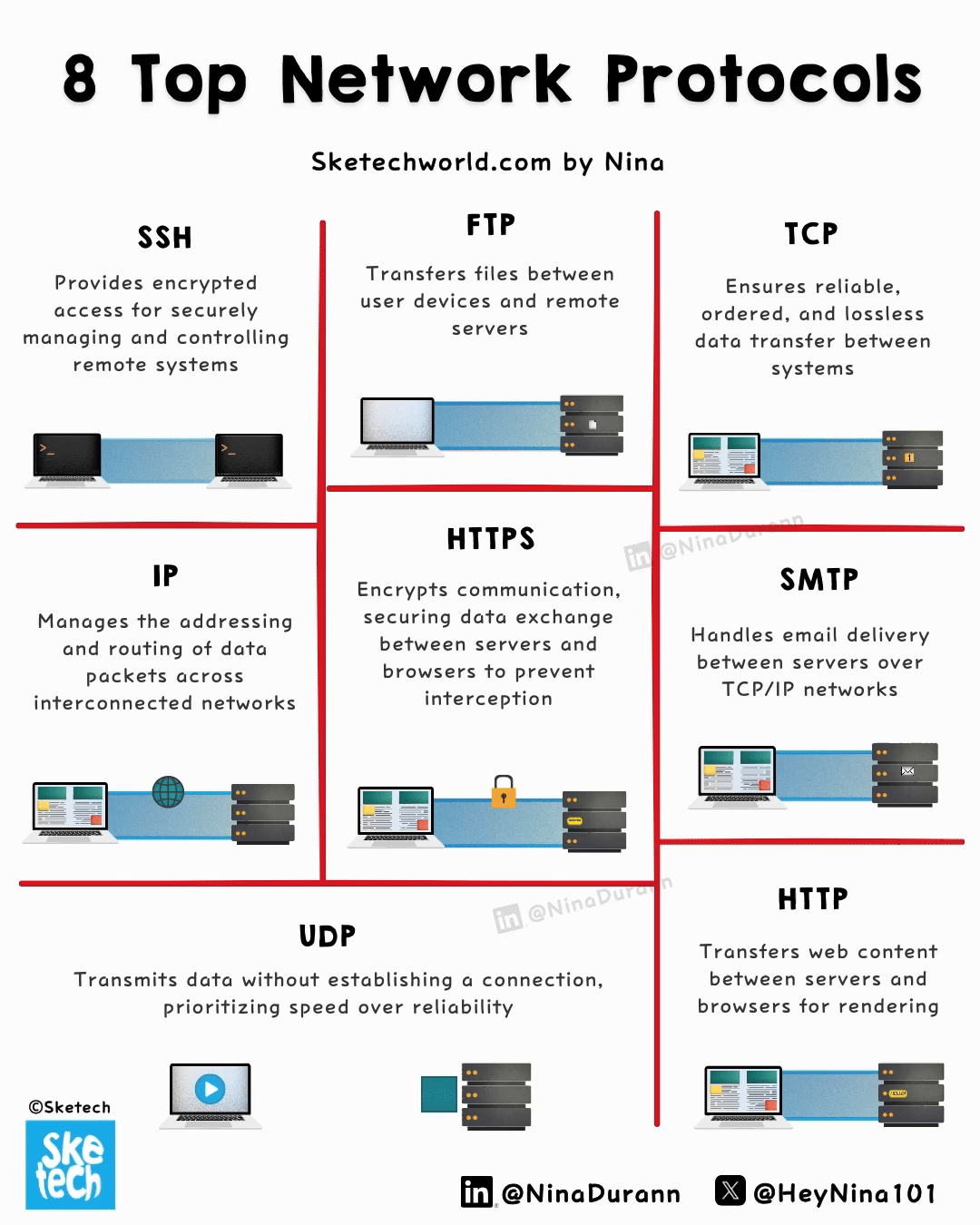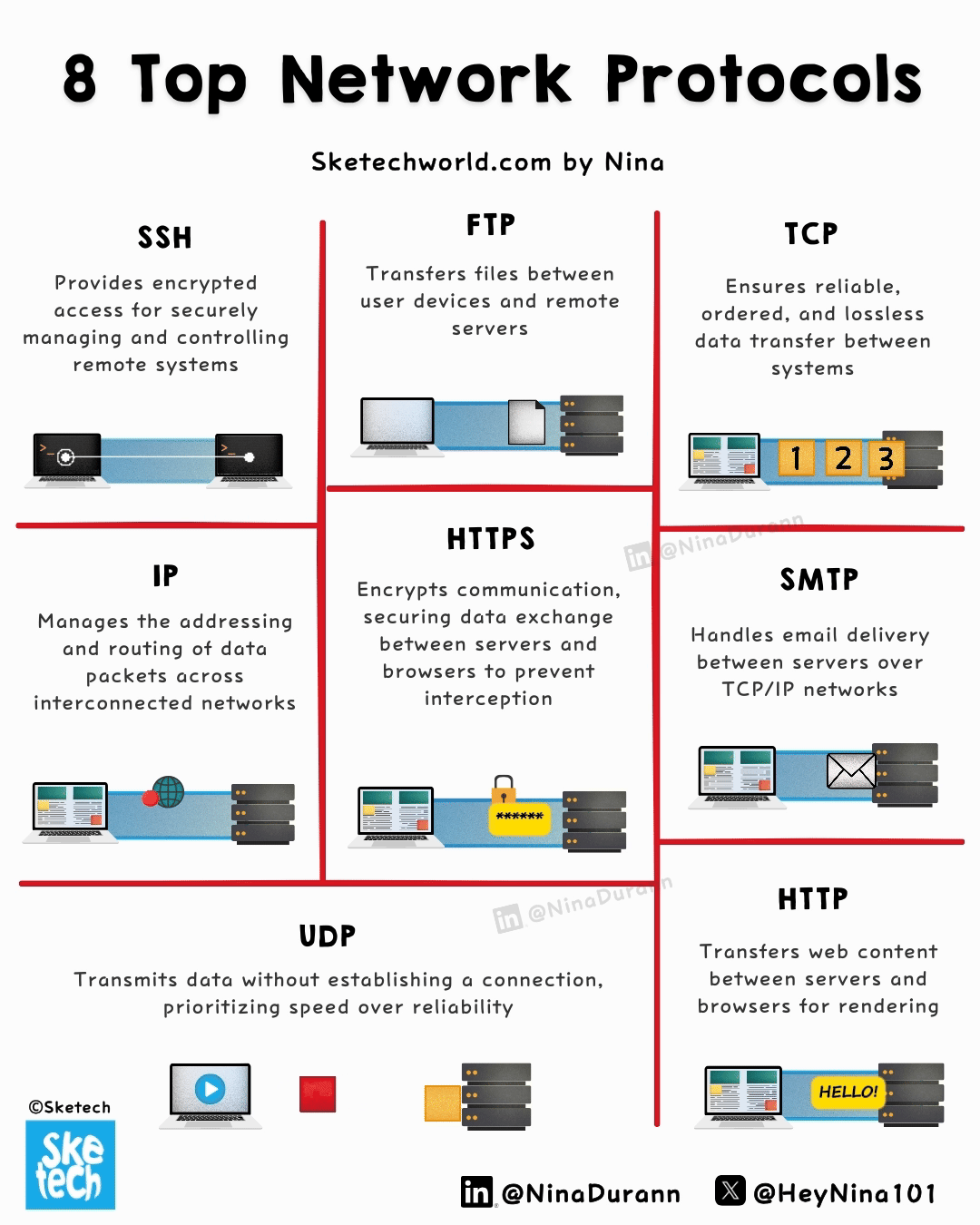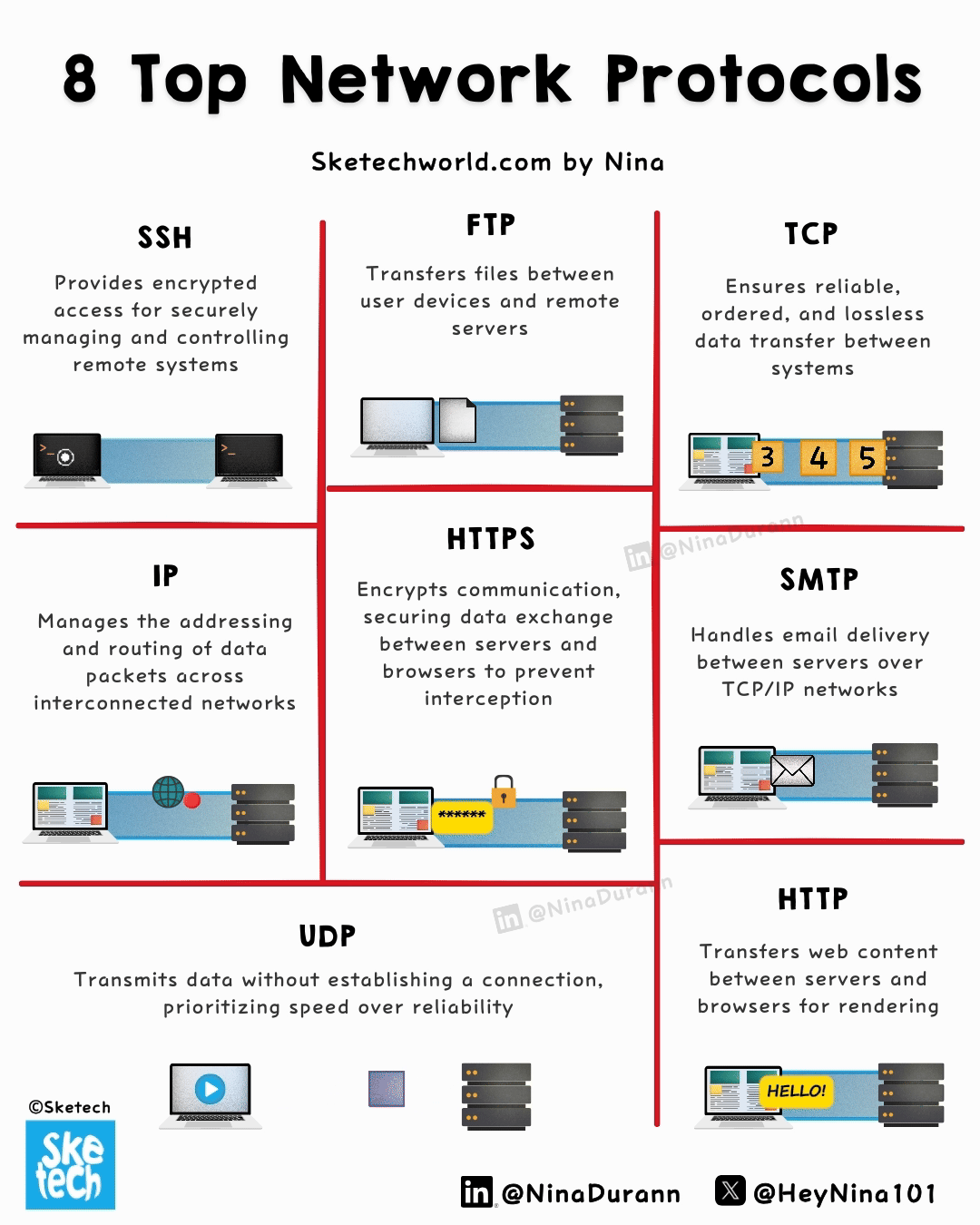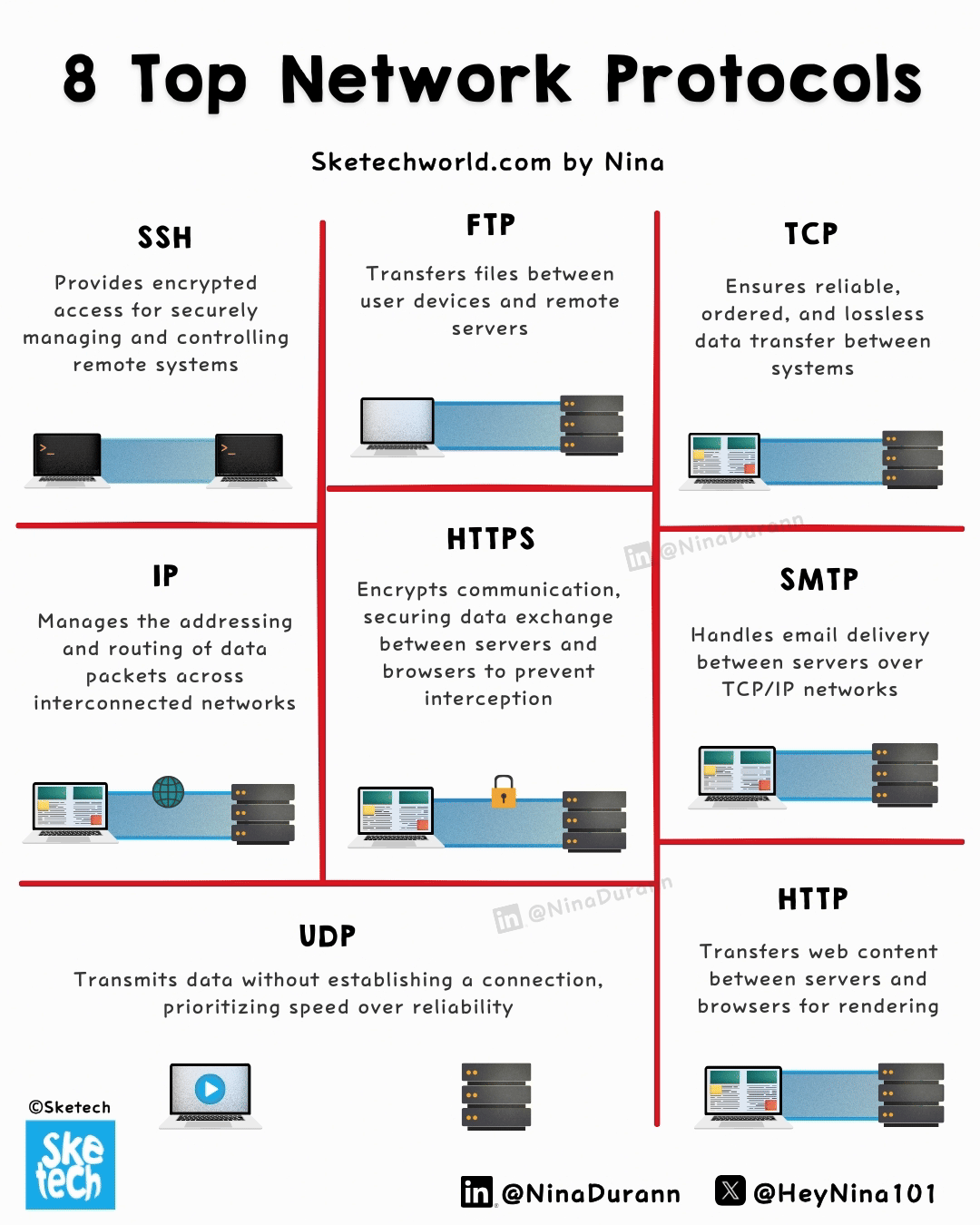
8 Network Protocols Explained in a Simple Way
Every online interaction relies on protocols; here are the 8 that form the core of modern connectivity.
↳ HTTP (HyperText Transfer Protocol) → Stateless protocol that governs the transfer of hypertext documents between clients and servers.
It operates over TCP and supports methods like GET, POST, DELETE … making it integral to web browsing and API interactions.
↳ HTTPS (HTTP Secure) → An extension of HTTP, HTTPS adds encryption via TLS, ensuring data integrity and confidentiality.
By encrypting data in transit, it protects against man-in-the-middle attacks, making it indispensable for secure transactions and user authentication.
↳ FTP (File Transfer Protocol) → Designed for transferring files over a network, FTP operates using separate channels for control (commands) and data transfer.
↳ TCP (Transmission Control Protocol) → Establishes a connection-oriented session, using handshakes to ensure data integrity.
It breaks data into packets, reassembles them in order, and provides retransmission in case of loss, making it vital for applications like email and file transfer.
↳ IP (Internet Protocol) → Routes packets across networks using unique identifiers.
IPv4, the most common version, uses 32-bit addresses, while IPv6, its successor, offers 128-bit addresses to accommodate global expansion and enhanced features.
↳ UDP (User Datagram Protocol) → Connectionless, prioritizing low latency over reliability. With no error checking or retransmission,
it’s ideal for applications like VoIP, live video streaming, and gaming, where speed is more critical than packet loss.
↳ SMTP (Simple Mail Transfer Protocol) → Handles the sending and relaying of emails across TCP/IP networks.
It establishes communication between mail servers and ensures reliable email delivery, forming the backbone of email communication worldwide.
↳ SSH (Secure Shell) → Provides secure access to remote systems by encrypting commands, data, and authentication credentials.
Widely used for system administration and file transfers, SSH employs public-key cryptography for secure key exchange and supports tunneling to protect data in transit.
Would you add any others?
5 Steps to Understand How VPN Tunneling Works
By encrypting and rerouting traffic, a VPN ensures your data travels securely online. Here’s how it works:
User Request:
The user initiates a request. The original packet contains the source IP (your device), the payload (data), and the destination IP (the server you’re trying to reach).
VPN Client Encryption:
The VPN client on your device encrypts the request (packet), encapsulates it inside another IP packet, and changes the destination IP to the VPN server’s IP.
Secure Tunnel:
The encrypted packet travels through the secure VPN tunnel to the VPN server.
VPN Server Decryption:
The VPN server receives and decrypts the packet, restoring the original payload. It replaces the source IP with its own to ensure your device’s IP remains hidden.
Delivery to Destination:
The VPN server forwards the modified packet to the final destination (e.g., a website or server).
This process secures your data, encrypting sensitive information and masking your real IP address to protect your online privacy.
7 Smart Strategies to Reduce Latency
Latency is a critical factor in application performance. Reducing it can improve user experience, boost efficiency, and scale systems effectively. Here are 7 proven strategies to optimize latency:
Distribute Traffic with Load Balancers
Evenly distribute traffic across servers to prevent bottlenecks and ensure smooth operation.
Use a CDN to Deliver Content Faster
Store static content closer to users, significantly reducing response times by minimizing data travel.
Compress Data for Faster Transfers
Reduce file sizes to accelerate data transfer speeds and cut bandwidth usage.
Implement Caching for Quick Data Retrieval
Retrieve pre-stored data instead of reprocessing it, speeding up repeated requests and reducing database load.
Process Tasks Asynchronously
Use workers to handle resource-intensive tasks in the background, freeing up system resources for faster responses.
Optimize Database Connections with Connection Pooling
Reuse database connections to reduce the overhead of creating new ones and improve interaction speeds.
Index Your Database for Faster Queries
Optimize searches by indexing your database, reducing query times and enhancing overall performance.
By implementing these strategies, you address latency at multiple layers of your system, from network optimization to backend processing.
What other strategies would you add to this list?
And that’s a wrap for Sketech Edition #18!
We’re growing fast—2,000 subscribers are just around the corner! Your support drives this journey, and this week, we hit another milestone: our very first pledge! Huge thanks for being part of this—let’s keep building something amazing together.
If you found this edition valuable, let me know - drop a ❤️!
See you in the next one.
Nina
Sketech Newsletter Bold and Fun Tech Visuals that Stick ❤️




True, great analogy! Glad you like it 😊. Thanks so much, Rafa!
TCP is like the friend who calls back to confirm you got their message; UDP is the one who just sends a text and leaves you guessing!
I enjoyed the strategies to reduce latency. Thank you, Nina.