In today’s episode of The Sketech Podcast, we break down cybersecurity in clear, actionable terms.
With our AI hosts, Bard and Lane, we examine the tactics and threats that put online security at risk: phishing, ransomware, SQL injection, DNS spoofing and more.
Each segment reveals how these attacks work, why they’re so effective, and specific steps you can take to protect your data.
In this episode
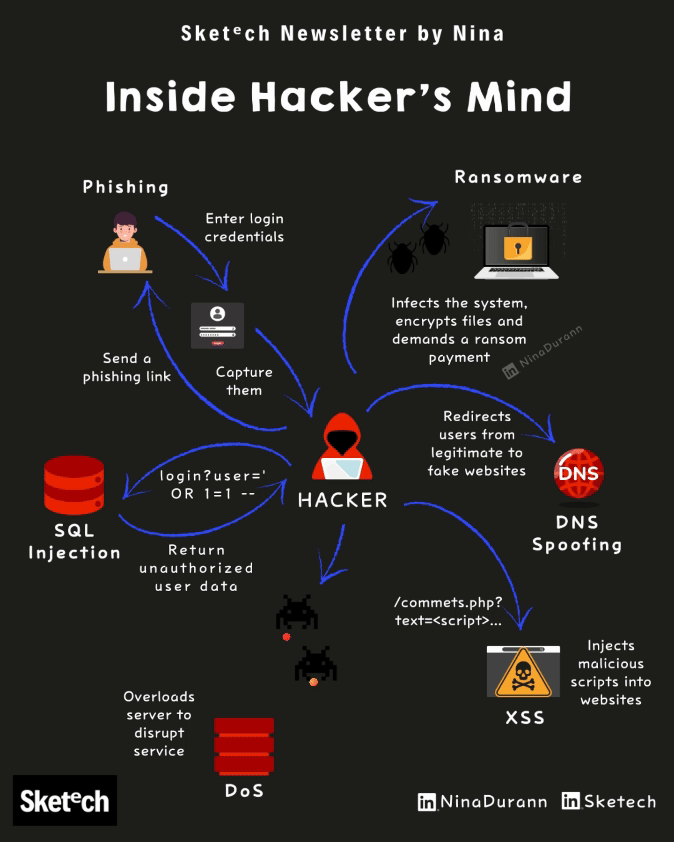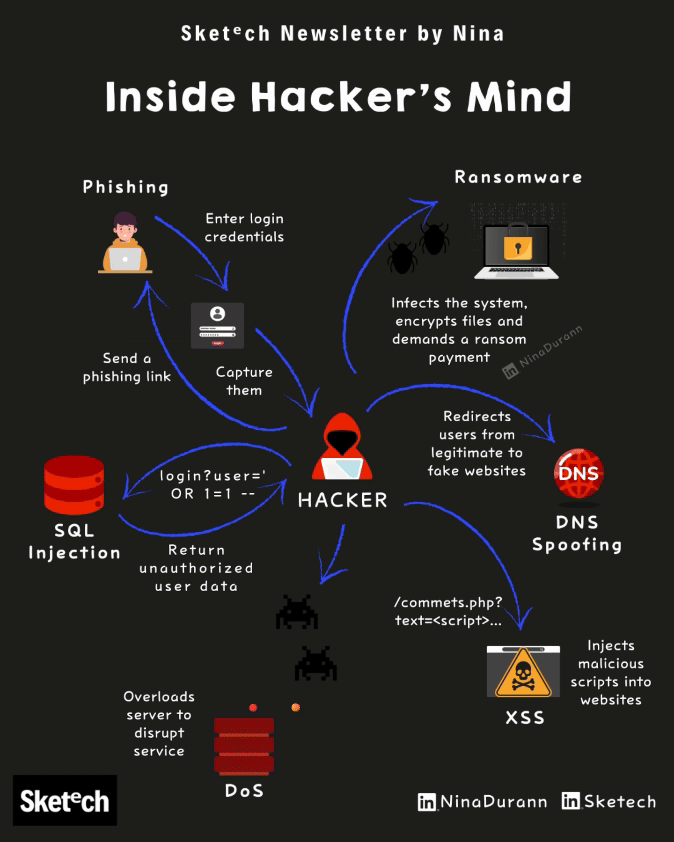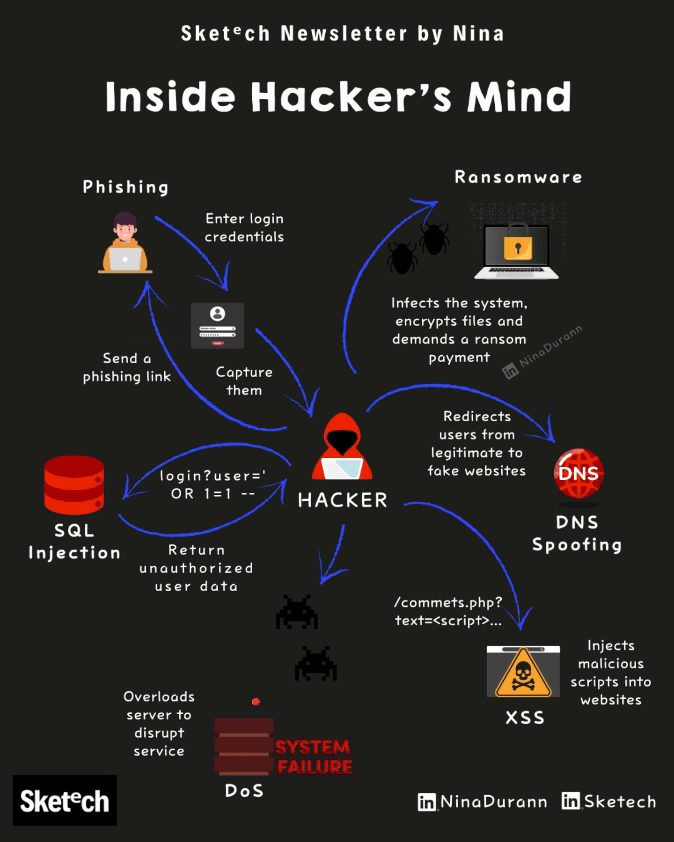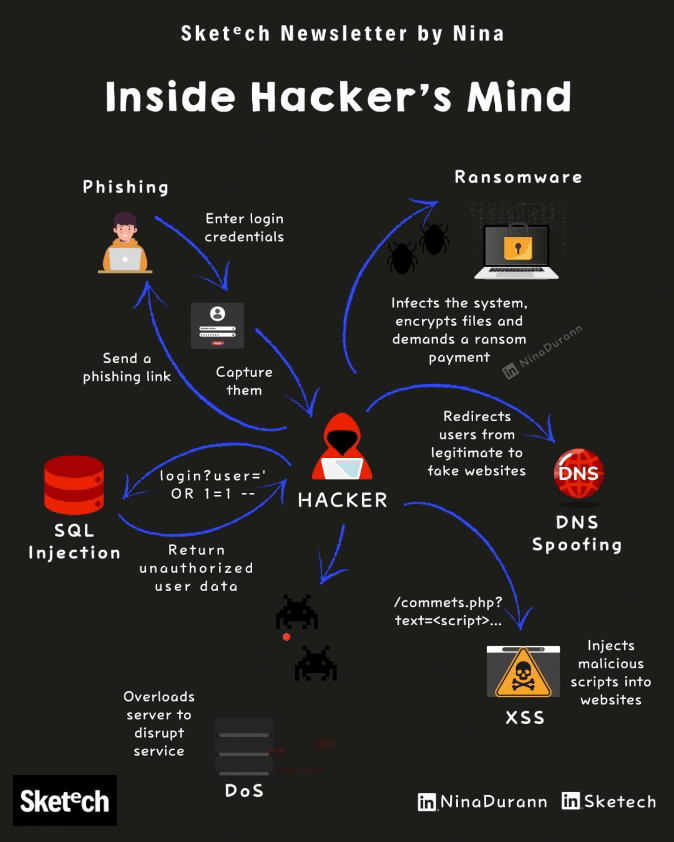
Phishing: The manipulation behind suspicious emails and links.
Ransomware: What happens when your data is held hostage.
SQL Injection: How attackers gain unauthorized access to databases.
DNS Spoofing: How fake websites trick legitimate users.
DDoS Attacks: Server overload and its impact on critical services.
XSS: Malicious scripts hiding in trusted sites.
Produced with AI for clear analysis and practical security strategies. Tune in to gain a precise view on how to face these threats.
I'm Nina, Software Project Manager and Visual Thinker of Sketech, my personal project where I turn complex software concepts into visuals and now into Podcasts. Follow me on LinkedIn for more insights.
Additional resources
OWASP Top Ten A comprehensive list detailing the ten most critical web application security risks, essential for recognizing and mitigating common threats.
Have I Been Pwned A tool that allows you to check if your email address has been compromised in any data breaches.
VirusTotal A free service that analyzes files and URLs for viruses, worms, trojans, and other kinds of malicious content.
Wireshark An open-source network protocol analyzer that enables you to capture and interactively browse the traffic running on a computer network
Inside Hacker’s Mind: 6 Cyber Attacks Explained Breakdown of common cyber attack methods and how they target vulnerabilities.
Need-to-Knows
What is phishing and how can I protect myself from it?Phishing is a cyberattack where hackers deceive users into providing sensitive information like passwords or credit card details by posing as a legitimate entity, often through emails or social media. To protect yourself:
Be cautious of suspicious emails or messages, especially those requesting personal information or containing urgent requests.
Always verify the sender's identity before clicking on links or opening attachments.
Enable two-factor authentication (2FA) on your accounts to add an extra layer of security.
Utilize email filtering to block spam and phishing attempts.
What is ransomware and how does it spread?Ransomware is a type of malware that encrypts your files, making them inaccessible. Hackers then demand a ransom, usually in cryptocurrency, to decrypt them. Ransomware often spreads through:
Phishing emails: Opening malicious attachments or clicking on links can download the ransomware onto your device.
Exploit kits: These target vulnerabilities in software to install ransomware without the user's knowledge.
How can I protect my system from ransomware attacks?While no system is entirely immune to attacks, these steps significantly reduce your risk:
Regular backups: Back up your important files regularly to a separate location (external hard drive or cloud storage) so you can restore them if your data is encrypted.
Patch management: Keep your operating system and software updated with the latest security patches to fix vulnerabilities that ransomware could exploit.
Endpoint detection and response (EDR): Utilize security software that monitors and detects suspicious activity on your devices.
Network segmentation: Divide your network into smaller, isolated segments to limit the spread of ransomware if an infection occurs.
What is SQL injection, and how can websites prevent it?SQL injection is a code injection technique that manipulates database queries to gain unauthorized access to sensitive data. Websites can mitigate this risk by:
Using prepared statements: These pre-compile SQL queries, preventing malicious code injection.
Validating user inputs: Check all user-submitted data (from forms, search bars, etc.) for unexpected characters or patterns before processing them.
Employing web application firewalls (WAF): WAFs act as a barrier between a website and incoming traffic, filtering out malicious requests.
What is DNS spoofing and how does it work?DNS spoofing, also known as DNS cache poisoning, redirects users from legitimate websites to malicious ones by corrupting DNS servers. This happens by:
Compromising DNS servers: Hackers can alter the DNS records on a server to point to their fake websites.
Exploiting vulnerable routers: Home or office routers with security flaws can be compromised to redirect traffic.
How can I protect myself from DNS spoofing attacks?Protecting yourself involves using secure DNS practices:
DNSSEC (DNS Security Extensions): This protocol digitally signs DNS data, ensuring its authenticity and preventing tampering.
Secure DNS resolvers: Choose reliable DNS resolvers like Google Public DNS or Cloudflare DNS, which have robust security measures.
Cache validation: Enable DNS cache validation on your router to check the integrity of cached DNS records.
What are denial-of-service (DoS) attacks, and what are the common defenses?DoS attacks overwhelm a server with excessive requests, making it unavailable to legitimate users. Effective defenses include:
Rate limiting: Restricting the number of requests a single source can make within a specific timeframe.
Traffic filtering: Identifying and blocking suspicious traffic patterns associated with DoS attacks.
Load balancing: Distributing traffic across multiple servers to prevent any single server from becoming overloaded.
DDoS mitigation services: Third-party services specialize in detecting and mitigating large-scale DoS attacks.
What is cross-site scripting (XSS), and how can websites protect against it?XSS attacks inject malicious scripts into trusted websites. When a user visits the infected site, the script executes in their browser, potentially stealing data or impersonating them. Websites can defend against XSS by:
Content Security Policy (CSP): Defining rules for what content the browser is allowed to load, blocking malicious scripts from untrusted sources.
Input sanitization: Cleaning user-submitted data to remove potentially harmful code before processing or displaying it.
Output encoding: Encoding special characters in the output to prevent them from being interpreted as code by the browser.
Study Guide
Cyber Attack 101: Understanding Common Threats
Short Answer Quiz
Instructions: Answer the following questions in 2-3 sentences each.
What is the primary goal of a phishing attack, and how is it typically carried out?
Explain the difference between a DoS and a DDoS attack.
How does ransomware affect a victim's data, and what is the attacker's objective?
Describe how SQL injection exploits vulnerabilities in web applications.
What is DNS spoofing, and how does it impact users?
How can two-factor authentication (2FA) help protect against phishing attempts?
Explain the role of regular backups in mitigating the impact of a ransomware attack.
What is the purpose of a web application firewall (WAF) in defending against SQL injection?
How does DNSSEC enhance security against DNS spoofing attacks?
What is the importance of input sanitization in preventing cross-site scripting (XSS) attacks?
Answer Key
Phishing aims to trick users into revealing sensitive information, such as login credentials or financial data. Attackers typically impersonate trustworthy entities through emails, SMS messages, or social engineering tactics.
A DoS (Denial of Service) attack overwhelms a server with traffic from a single source, disrupting its service. A DDoS (Distributed Denial of Service) attack utilizes multiple compromised systems to flood the target, making it more difficult to defend against.
Ransomware encrypts a victim's files, rendering them inaccessible. Attackers demand a ransom payment, often in cryptocurrency, in exchange for the decryption key.
SQL injection manipulates database queries by inserting malicious code into web application inputs, such as login forms or search bars. This allows attackers to bypass security measures and access sensitive data.
DNS spoofing, or DNS cache poisoning, redirects users from legitimate websites to malicious ones by altering DNS records. Users believe they are visiting a trusted site, but their traffic is directed to a site controlled by the attacker.
Two-factor authentication (2FA) requires users to provide two forms of identification, typically something they know (password) and something they have (a code from a mobile device). This makes it significantly harder for attackers to gain access to accounts even if they obtain a password through phishing.
Regular backups provide a copy of data that can be restored in case of data loss, such as from a ransomware attack. This allows victims to recover their files without paying the ransom.
A web application firewall (WAF) acts as a barrier between web applications and potential attackers. It analyzes incoming traffic, filters malicious requests and blocks attempts to exploit vulnerabilities, such as SQL injection.
DNSSEC (Domain Name System Security Extensions) adds digital signatures to DNS records, ensuring their authenticity and integrity. This helps prevent attackers from spoofing DNS records and redirecting users to malicious sites.
Input sanitization removes potentially harmful characters and code from user-supplied data before processing it. This mitigates the risk of cross-site scripting (XSS) attacks, where malicious scripts are injected into websites.
Essay Questions
Critically analyze the impact of social engineering tactics used in phishing attacks and evaluate the effectiveness of user education programs in mitigating this threat.
Compare and contrast the motivations and methodologies of cyber attackers who deploy ransomware versus those who engage in denial-of-service attacks.
Discuss the ethical implications of paying ransoms to cybercriminals in response to ransomware attacks. Consider the potential consequences for both individual victims and society as a whole.
Explain the concept of "defense in depth" as it relates to cybersecurity. Provide specific examples of how organizations can implement layered security measures to protect against various cyber threats.
In the face of increasingly sophisticated cyberattacks, how can governments and private industry collaborate effectively to enhance cybersecurity awareness, improve incident response capabilities, and strengthen legal frameworks for cybercrime prosecution?
Glossary of Key Terms
Cyberattack A deliberate attempt to exploit vulnerabilities in computer systems or networks to gain unauthorized access, steal data, disrupt operations, or cause damage.
Phishing A social engineering technique used to trick individuals into revealing sensitive information by impersonating legitimate entities.
Ransomware Malicious software that encrypts files, rendering them inaccessible until a ransom is paid.
SQL Injection A code injection technique used to exploit vulnerabilities in web applications and gain unauthorized access to databases.
DNS Spoofing Redirecting internet traffic from legitimate websites to malicious ones by altering DNS records. Also known as DNS cache poisoning.
DoS/DDoS Attack Overloading a server with excessive requests to disrupt its service. DDoS involves multiple compromised systems.
Cross-Site Scripting (XSS) Injecting malicious scripts into websites to steal data or impersonate users.
Two-Factor Authentication (2FA) Requiring two forms of identification for authentication, enhancing security against password theft.
Web Application Firewall (WAF) A security layer that filters malicious traffic to protect web applications from attacks like SQL injection and cross-site scripting.
DNSSEC A set of security extensions for the Domain Name System that adds digital signatures to DNS records, ensuring their authenticity and integrity.
Input Sanitization Removing potentially harmful characters and code from user-supplied data before processing to prevent attacks like cross-site scripting.
Defense in DepthA cybersecurity strategy employing multiple layers of security measures to protect systems and data.
Social EngineeringManipulating individuals into performing actions or divulging confidential information through psychological tactics.
Linkedin Post
Inside Hacker’s Mind: 6 Cyber Attacks Explained










Share this post