How API Pagination, Kafka Use Cases and Security Practices Solve Data Handling, Scalability and Protection Challenges Sketech #16
Actionable strategies to tackle data management enhance API security, and scale systems effectively
Hi, Nina here. Ever notice how some ideas just click when presented the right way?
This week, I’m revisiting the most-loved visuals and posts from social media, the ones that sparked real conversations and made tough concepts feel simple.
Here’s what’s waiting for you:
API Pagination Techniques Explained → Master the strategies to keep your data flowing smoothly without breaking a sweat.
5 Top Apache Kafka Use Cases Clearly Explained → Real-world examples that prove why Kafka is essential for scaling modern systems.
API Security Guide: Best Practices → Cut through the noise with simple, actionable steps to secure your APIs.
Python List Methods → A handy breakdown of the most practical methods you’ll use every day.
API Pagination Techniques Explained
When an API handles large datasets, poor pagination can quickly become a bottleneck
Four Common Pagination Methods
Offset-based pagination: Relies on
limitandoffsetparameters to paginate.Limitspecifies how many items to return andoffsetdefines where to start in the dataset.Cursor-based pagination: Instead of relying on numerical offsets, the server generates a cursor to identify the starting point for the next page. Ideal for datasets where new entries are frequently added or removed.
Keyset-based pagination: Uses a stable key (e.g.,
ID,timestamp) to paginate efficiently in large datasets. This method bypasses row counting, improving speed and scalability.Page-based pagination: Retrieves data using a
pageparameter (e.g.,?page=3) to specify which subset of data to return. It’s simple and intuitive but less effective in datasets that change frequently.
How to Implement Pagination in Your API
Offset-based Pagination: GET /items?limit=10&offset=20
This request returns 10 items starting from the 21st record.
Cursor-based Pagination: GET /items?cursor=abc123
The server provides a
cursorlikeabc123for the next page, allowing precise control over the data flow.Keyset-based Pagination: GET /items?after_id=100
This request retrieves items where the
IDis greater than 100, efficiently leveraging indexed fields.Page-based Pagination: GET /items?page=3
Fetches the third page of results, with each page containing a predefined number of items.
Avoid These 3 Common Pagination Mistakes
Neglecting the last page: Ensure your API returns a clear response when users reach the final page of data.
Failing to account for real-time data: Use cursor-based or keyset-based pagination to avoid issues with missing or duplicated records in dynamic datasets.
Ignoring documentation: Clearly explain your pagination parameters (
limit,offset,cursor,page) in your API documentation to avoid confusion.
Best Practices
Optimize database queries: Use indexes on fields you paginate (e.g.,
ID,timestamp).Set a maximum page size: Protect your system by capping the number of items per page.
Validate pagination parameters: Ensure
limitandoffsetvalues are valid to prevent errors.Consistency across endpoints: Keep pagination formats uniform to maintain ease of use and prevent confusion.
What’s the biggest mistake you’ve seen in API pagination?
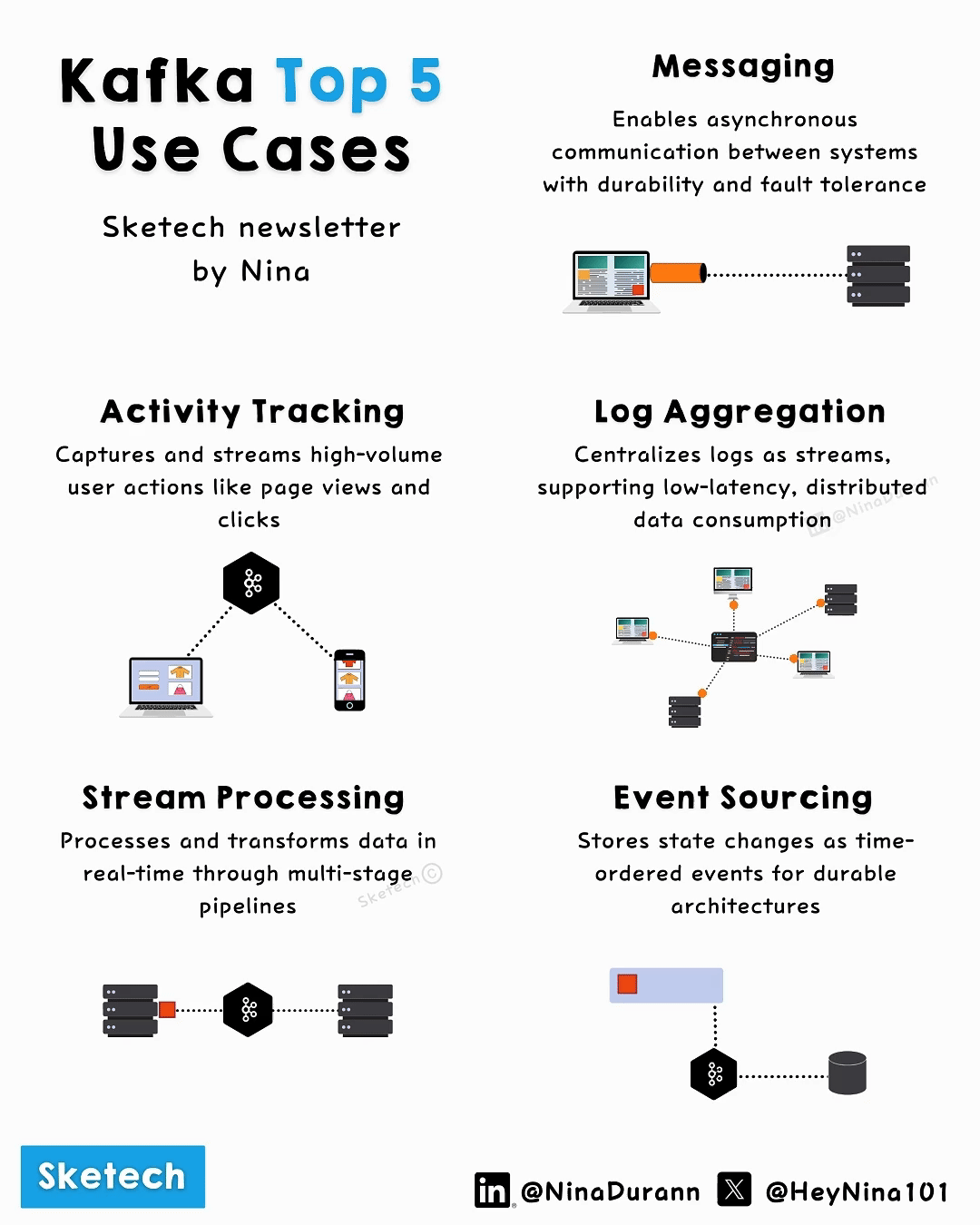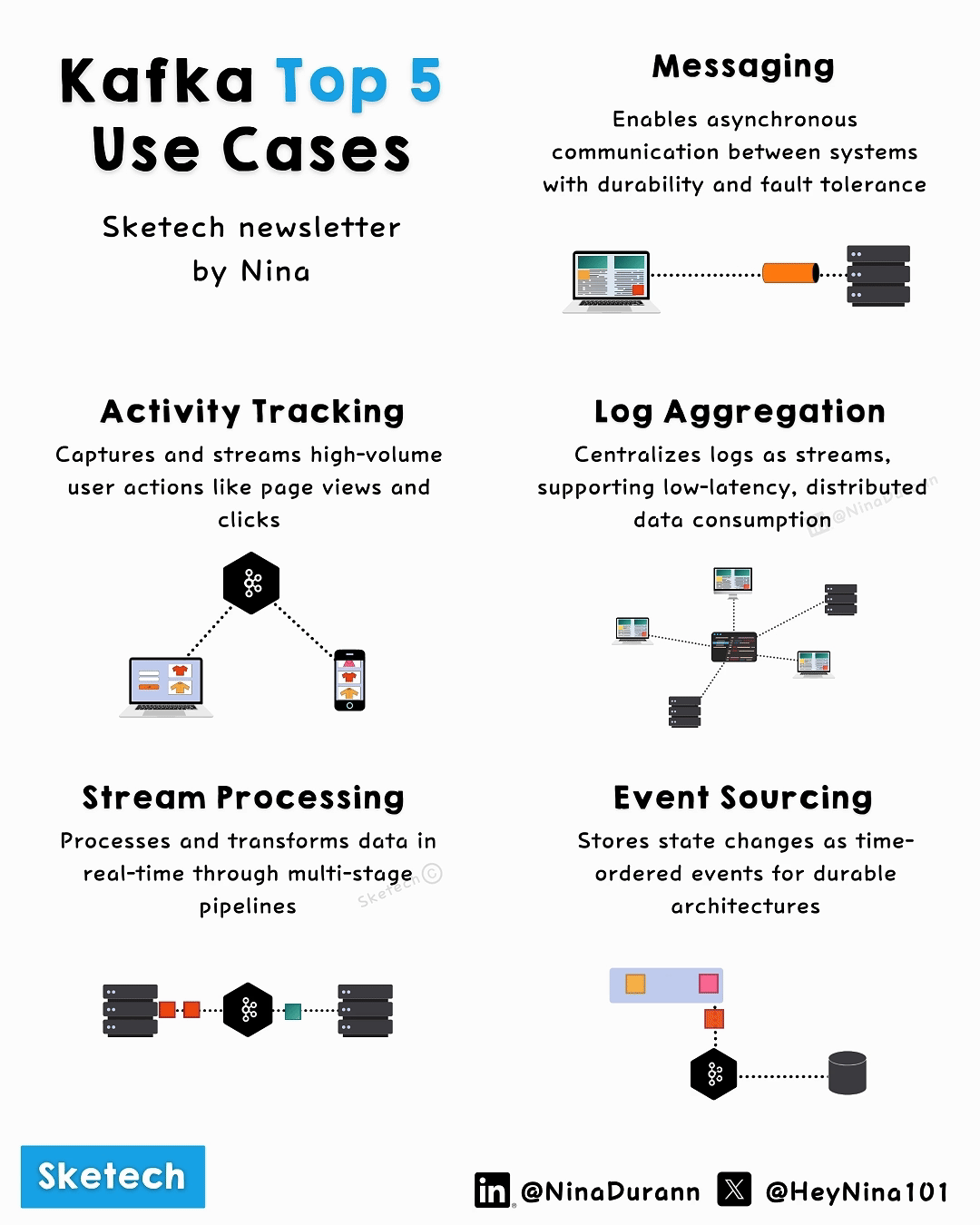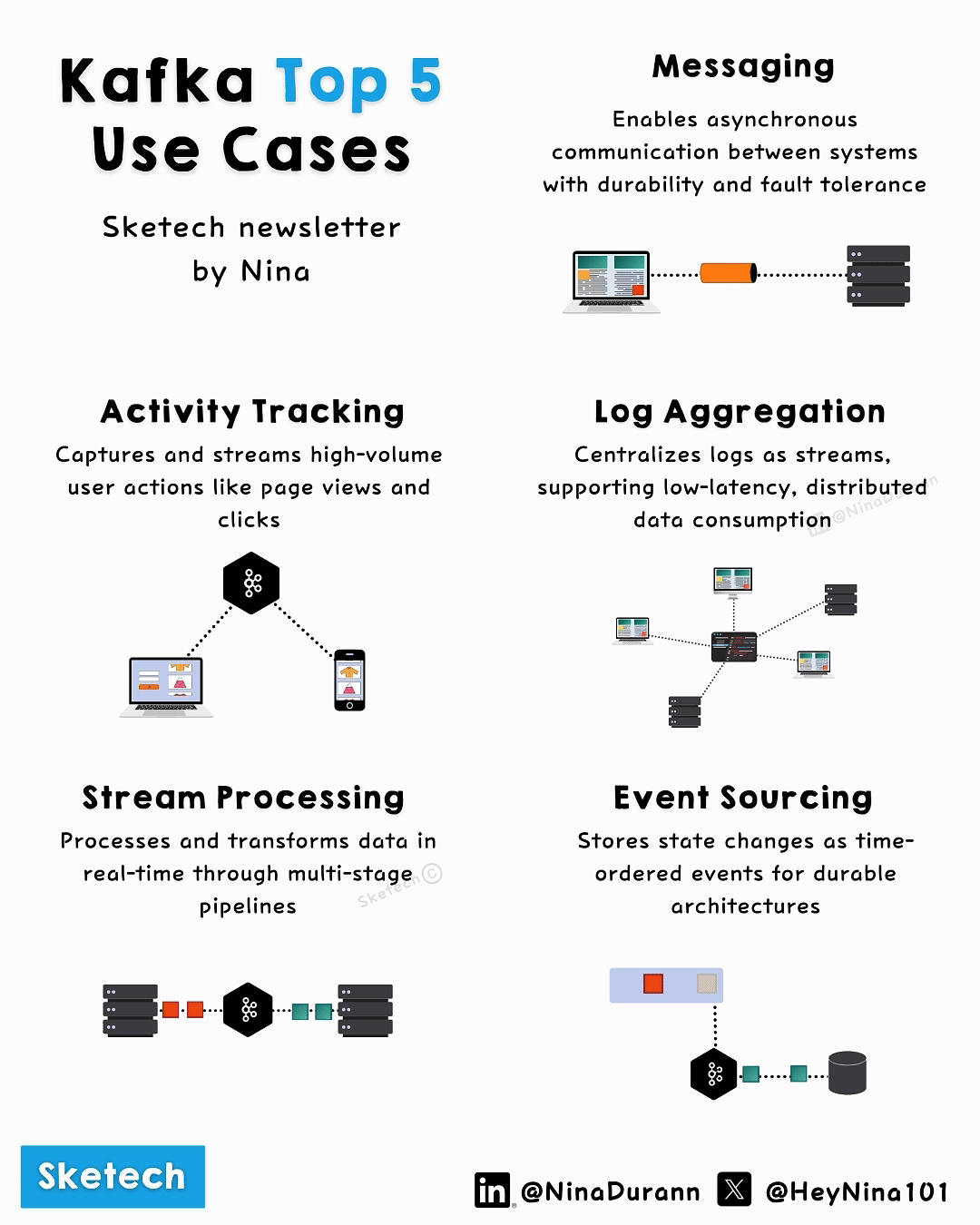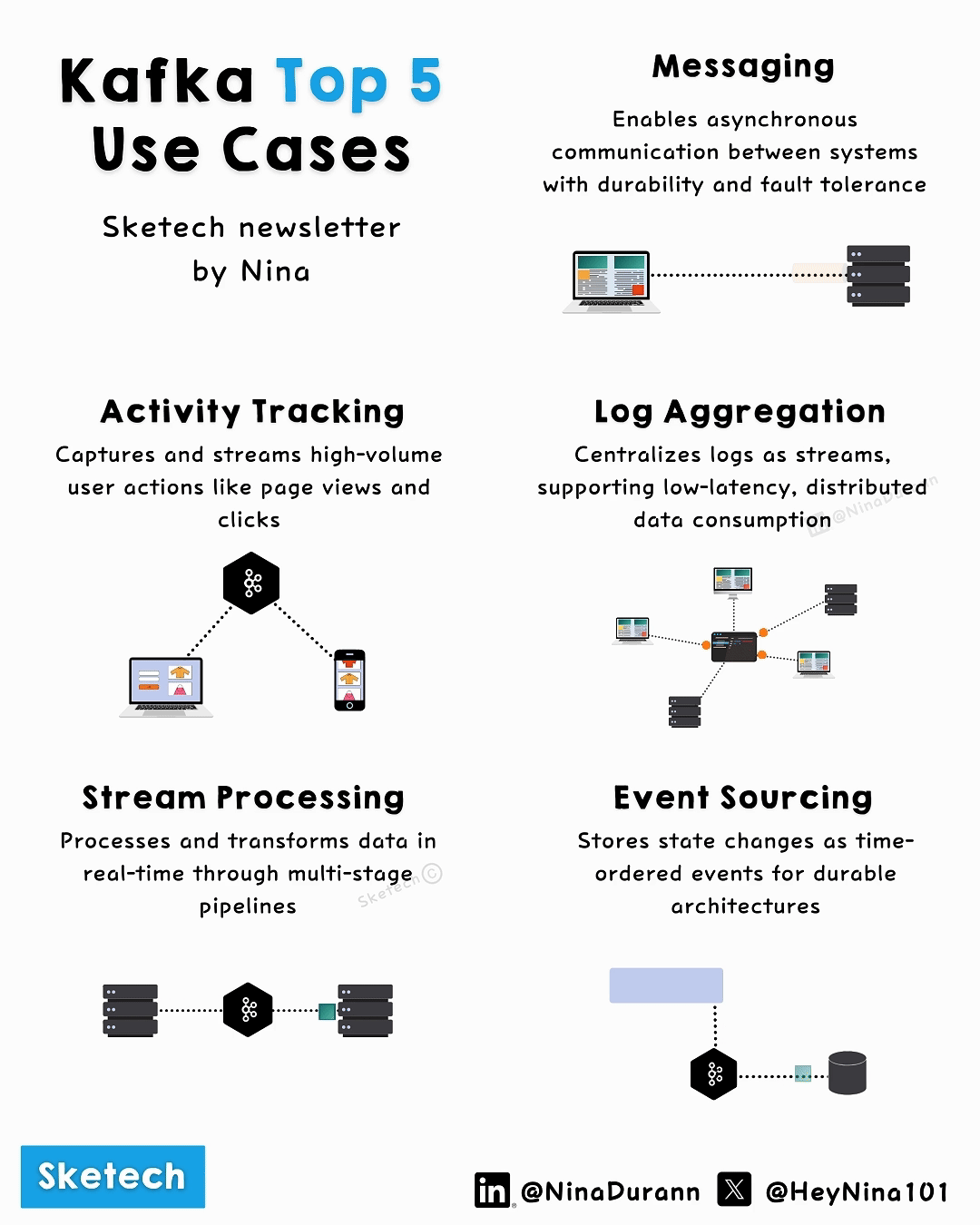
5 Top Apache Kafka Use Cases Clearly Explained
Apache Kafka is a distributed platform widely adopted for managing real-time data and events at scale. Its versatility makes it essential in modern architectures, providing solutions for messaging, data processing, and event logging through its partition-based model and high-availability architecture.
Here's a comprehensive description of its top use cases:
1. Messaging
Asynchronous communication between producers and consumers
Decouples systems for better scalability and reliability
Offers high throughput with partition-based scaling
Provides different delivery guarantees (at-least-once, exactly-once)
2. Activity Tracking
Captures user actions like clicks, page views, and searches
High-throughput, handling millions of events per second
Used in real-time analytics and behavioral monitoring
Maintains event order within partitions for accurate sequencing
3. Log Aggregation
Centralizes logs from distributed systems into structured streams
Low-latency processing with distributed data consumption
Common for debugging and system performance analysis
Supports long-term storage with configurable retention policies
4. Stream Processing
Processes, transforms, and enriches data in real-time pipelines
Multi-stage workflows
Ideal for IoT data, financial systems, and data transformations
Supports stateful operations and windowed computations
5. Event Sourcing
Logs state changes as immutable, time-ordered events
Enables application state reconstruction and traceability
Supports multiple read projections from the same event log
Used in audit systems and event-driven architectures
Maintains complete system history for compliance and debugging
Key Technical Features:
Partition-based distribution for scalability
Replication for fault tolerance
ZooKeeper/KRaft for cluster coordination
Consumer groups for parallel processing
Configurable durability and consistency guarantees
Kafka continues to prove its value in handling real-time data and powering modern systems with flexibility and reliability.
API Security Guide: Best Practices
Every API exposed online is a potential threat entry point. Securing them requires controls, monitoring, and clear policies. This guide outlines key practices for protecting APIs across their lifecycle.
1. Authentication & Authorization
Use OpenID Connect and OAuth 2.0.
Access Control: Apply RBAC or ABAC.
API Keys: Store securely with secrets managers.
Token Rotation: Automate expiration and revocation.
💡 Restrict access to verified entities.2. Data Protection
Data Encryption at Rest
HTTPS: Enforce HSTS.
Input Validation: Prevent SQL Injection and XSS.
Key Rotation: Automate key updates.
💡 Keep data secure at rest and in transit.3. Traffic Management
Rate Limiting: Control request frequency.
DDoS Mitigation: Use Web Application Firewalls.
API Gateway: Centralize routing.
Timeouts: Avoid resource exhaustion.
💡 Ensure stable API performance.4. Monitoring
Continuous Monitoring: Use Prometheus or Datadog.
Audit Trails: Log anomalies.
Alerts: Detect traffic spikes.
💡 Respond to threats in real-time.5. Dependency Management
Update Libraries
Secure Configs: Enforce security policies.
Secrets Management: Avoid hardcoded credentials.
💡 Reduce dependency-related risks.6. API Versioning
Versioned APIs: Avoid breaking changes.
Deprecation Policies: Announce changes early.
💡Enable seamless version transitions.7. Development Security
Shift-Left Security: Integrate in CI/CD.
API Testing: Use tools like OWASP ZAP, Burp Suite, and Postman for penetration testing, vulnerability scanning, and functional validation.
💡 Build APIs securely from the start.8. Incident Response
Playbooks: Define response plans.
Drills: Test readiness.
💡 Minimize breach impact.Ignoring API security can open the door to serious risks. With the right practices in place, you can protect your APIs and keep your systems running smoothly and securely.
Python List Methods
Python lists offer a robust suite of methods essential for efficient data manipulation and algorithm design. Let’s break down the methods that truly matter, along with some practical insights.
Core Operations – Build and Reshape Efficiently
append(item) — Adds an element to the end of the list.→ Often used in data pipelines to accumulate results progressively.
remove(item) — Deletes the first occurrence of a specific value.→ Handy for cleaning data without relying on manual filtering.
insert(index, item) — Places an element at a specific position in the list.→ Useful when the order of items is critical.
pop([index]) — Removes and returns an element by its index.→ Commonly paired with append() in stack-based algorithms.
When combined, pop() and append() are the backbone of stack operations like Depth-First Search (DFS).
Data Analysis – Understand and Query Lists
count(item) — Returns how many times a value appears in the list.→ Quick way to profile data distributions.
index(item[, start[, end]]) — Finds the first position of a value.→ Essential when implementing search or validation logic.
sort(key=None, reverse=False) — Sorts elements in place, with optional custom rules.→ Perfect for ranking systems or when dealing with complex objects.
reverse() — Flips the order of the list in place.→ Often used in undo mechanisms or step-back features.
The key parameter in sort() is a game-changer, letting you sort elements by attributes or custom criteria.
Data Management – Ensure Integrity and State
copy() — Creates a shallow duplicate of the list.→ Prevents unintended changes when passing lists between functions.
clear() — Empties the list completely.→ Ideal for resetting temporary storage or cache structures.
When sharing lists across multiple components, copy() ensures each part works with an independent version, avoiding side effects.
With this cheat sheet, you’ll have the essential Python list methods ready to use, clear, concise, and practical for everyday coding.
And that wraps up this edition of Sketech! It’s always exciting to see how these ideas connect with you and spark new perspectives. Your curiosity and engagement keep this journey alive, and I’m grateful for it.
If this edition brought you value, let me know ❤️ your feedback means a lot!
Until next time,
Nina
Sketech Newsletter
Crafted to make concepts unforgettable 




Hi Nina, for offset use case. Any way to optimize count method for pagination. It’s always the problem for response time takes longer