Sketech #10 How SSO, Load Balancing and Network Protocols Solve the Everyday Challenges of Access, Speed and Connectivity
Get a clear, visual breakdown of how these key technologies work together to improve your systems and workflow
Hey! This week’s Sketech is here to make your work as a software developer just a bit clearer and more fun.
Here’s what we’re unpacking today:
Breaking down Single Sign-On (SSO) — make it simple and visual.
How Load Balancing Algorithms actually Work — a clear, detailed 2-in-1 Guide.
8 Must-Know Network Protocols — a quick and easy guide you’ll remember.
Breaking down Single Sign-On (SSO)
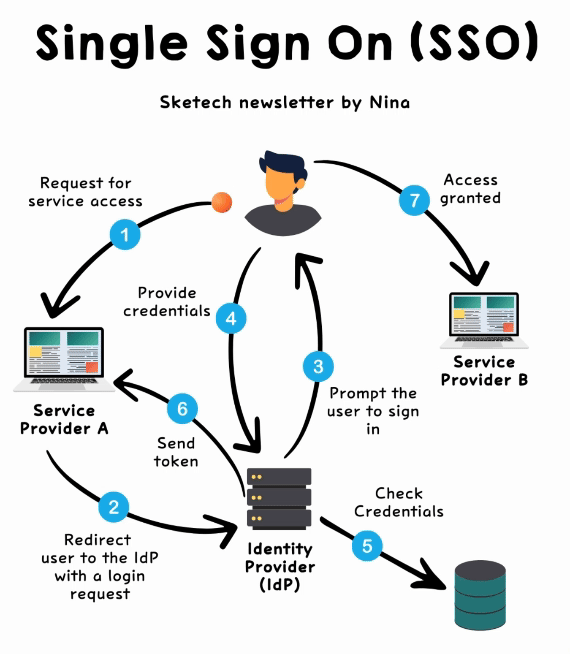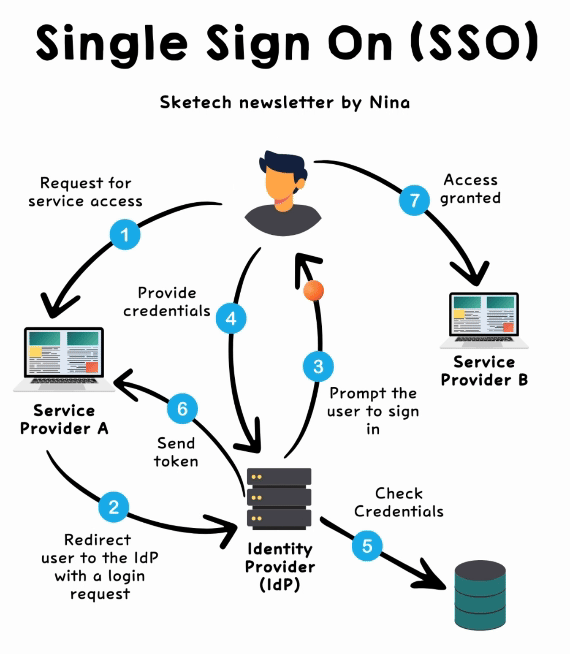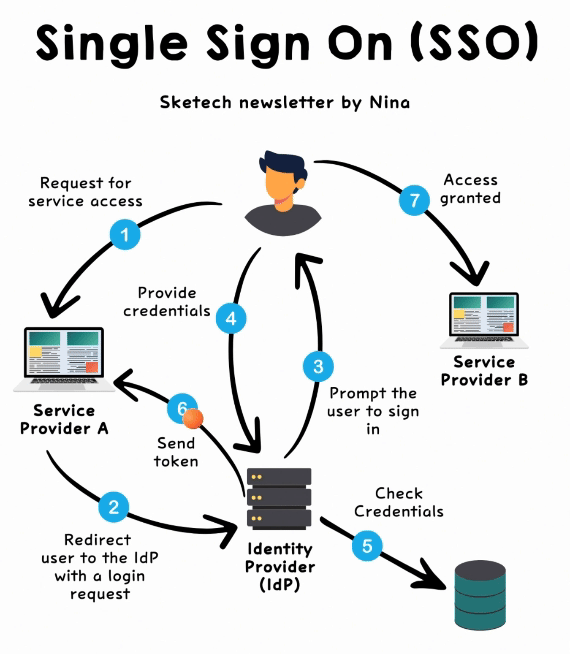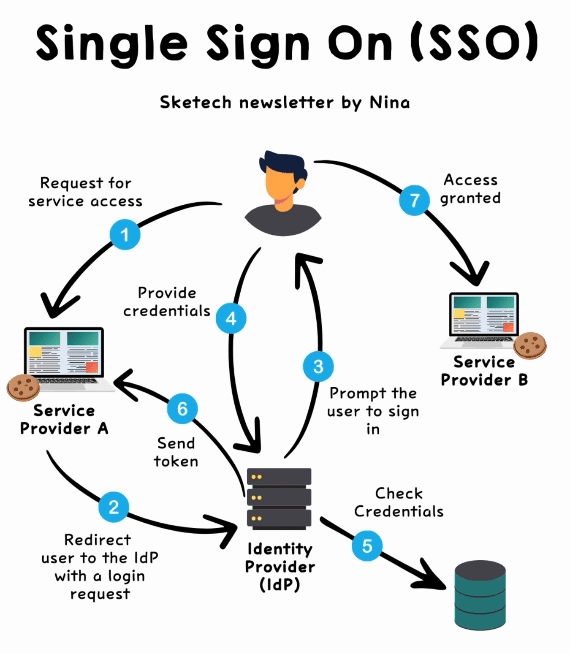
Single Sign-On lets users access multiple applications with one login. Here’s how it works behind the scenes:
1/ Request for service access → The user attempts to access a service (Service Provider A).
2/ Redirect to the Identity Provider (IdP) → Service Provider A redirects the user to the IdP with a login request.
3/ Prompt the user to sign in → The IdP asks the user to authenticate by entering their credentials (e.g., username, password, or MFA).
4/ Provide credentials → The user submits their credentials to the IdP for verification.
5/ Check credentials → The IdP verifies the user’s credentials against its database to confirm their identity.
6/ Send token → Once verified, the IdP generates a secure signed token (e.g., a SAML assertion or OAuth JWT) and sends it back to Service Provider A.
7/ Access granted → Service Provider A validates the token and grants access. The user can also seamlessly access other connected services (e.g., Service Provider B) without logging in again.
Why SSO Matters:
Reduces login fatigue and improves user experience.
Centralizes credential management, strengthening security.
Supports scalability in modern multi-service architectures.
Challenges:
Tokens must be encrypted and short-lived to avoid misuse.
Ensuring interoperability between services requires proper protocol configuration (e.g., OAuth, SAML, OpenID Connect).
The IdP must be highly available to avoid single points of failure.
SSO relies on tokens for seamless access, but what happens if a token is compromised? How do you mitigate the risk? Think about it
How Load Balancing Algorithms actually Work
Load balancing is a technique to distribute network traffic or workloads across multiple servers to ensure no single server becomes a bottleneck. Here are six simple load balancing algorithms:
1/ Round Robin (RR)
Sends requests cyclically to servers.
Best for non-session-persistent scenarios (e.g., static content).
Simple but assumes equal server capacity, leading to imbalance.
Struggles with uneven request processing times.
2 / Random
Distributes requests randomly.
Useful in testing or environments with low balancing precision needs.
Avoids sequential server exhaustion but doesn’t account for server capacity.
Over time, balances statistically
3/ Least Connections (LC)
Routes requests to the server with the fewest active connections.
Ideal for systems with variable session durations.
Requires real-time monitoring, adding complexity.
Less effective for uniform request durations.
4/ Weighted Least Connections (WLC)
Extends LC by factoring in server capacity.
Allocates more traffic to stronger servers.
Critical for environments with mixed hardware.
Requires accurate weight configuration for efficiency
5/ IP Hashing
Routes requests based on client IP for consistent handling.
Key for session persistence without cookies or in caching.
Can create imbalance with uneven IP distribution or NAT-shared IPs.
6/ Least Response Time (LRT)
Sends traffic to the server with the lowest response time.
Ideal for latency-sensitive or real-time systems.
Needs robust performance monitoring, adding overhead.
Implementation Tips
Monitoring: Use real-time tools for server health and performance.
Failover: Include backup mechanisms for seamless recovery.
Dynamic Adjustments: Update weights and thresholds in real-time for WLC and LRT.
Session Persistence: Ensure mechanisms handle edge cases like shared NAT IPs.
These six algorithms are among the most common, covering a wide range of use cases. However, more specialized approaches exist for unique scenarios, depending on the needs of your system.
8 Must-Know Network Protocols
Network Protocols Simplified: A Quick Guide to Get You Started
Every online interaction relies on protocols—here are the 8 that form the core of modern connectivity.
↳ HTTP (HyperText Transfer Protocol) → Stateless protocol that governs the transfer of hypertext documents between clients and servers.
It operates over TCP and supports methods like GET, POST, DELETE … making it integral to web browsing and API interactions.
↳ HTTPS (HTTP Secure) → An extension of HTTP, HTTPS adds encryption via TLS, ensuring data integrity and confidentiality.
By encrypting data in transit, it protects against man-in-the-middle attacks, making it indispensable for secure transactions and user authentication.
↳ FTP (File Transfer Protocol) → Designed for transferring files over a network, FTP operates using separate channels for control (commands) and data transfer.
↳ TCP (Transmission Control Protocol) → Establishes a connection-oriented session, using handshakes to ensure data integrity.
It breaks data into packets, reassembles them in order and provides retransmission in case of loss, making it vital for applications like email and file transfer.
↳ IP (Internet Protocol) → Routes packets across networks using unique identifiers.
IPv4, the most common version, uses 32-bit addresses, while IPv6, its successor, offers 128-bit addresses to accommodate global expansion and enhanced features.
↳ UDP (User Datagram Protocol) → Connectionless, prioritizing low latency over reliability. With no error checking or retransmission,
it’s ideal for applications like VoIP, live video streaming and gaming, where speed is more critical than packet loss.
↳ DNS (Domain Name System) → Resolves domain names into IP addresses through a distributed hierarchy of name servers.
It supports caching for performance and incorporates mechanisms like DNSSEC to enhance security against spoofing.
↳ SSH (Secure Shell) → Provides secure access to remote systems by encrypting commands, data and authentication credentials.
Widely used for system administration and file transfers, SSH employs public-key cryptography for secure key exchange and supports tunneling to protect data in transit.
Thanks for reading! I hope you’ve picked up a few ideas that spark new possibilities. Wishing you a productive week ahead—take care and keep pushing forward!
Nina
Sketech Newsletter
Crafted to make concepts unforgettable 🩵