Docker vs. Kubernetes: Who Does What?! - Not a Face-Off, but here 10 points to clear the confusion! + 5 Common Cyberattacks Explained - Sketech #20
You'll find 7 high-energy illustrations that help you experience Software Concepts in a new way, designed to make concepts stick and stay clear 🔥
Hey there! Nina here. Welcome to the free edition of the Sketech Newsletter!
Each week, you get bold, fun visuals and insights that make complex software engineering concepts click. Here are the topics that made waves in February:
Docker vs. Kubernetes: Who Does What? - Not a Face-Off, But Here 10 Points to Clear the Confusion!
5 Common Network Attacks Explained - At the end of the newsletter, you’ll find the full visual
Complete Visual Breakdown: 5 Common Network Attacks Explained
If you believe tech is exciting, challenging and epic, your like is what keeps this movement alive. Sketech isn’t just content; it’s a community that grows with every one of you. Your heart ♥️ keeps this energy growing!
A few years ago, while leading the migration of a monolithic application to microservices, I faced a challenge familiar to many in the cloud and DevOps world: how to efficiently manage dozens of containers in an environment that demanded scalability and resilience. That’s when I truly understood the importance of Docker and Kubernetes, not as competitors, but as complementary tools. Both are essential in cloud-native development and DevOps, but they serve distinct purposes.
Docker vs. Kubernetes: Who Does What?
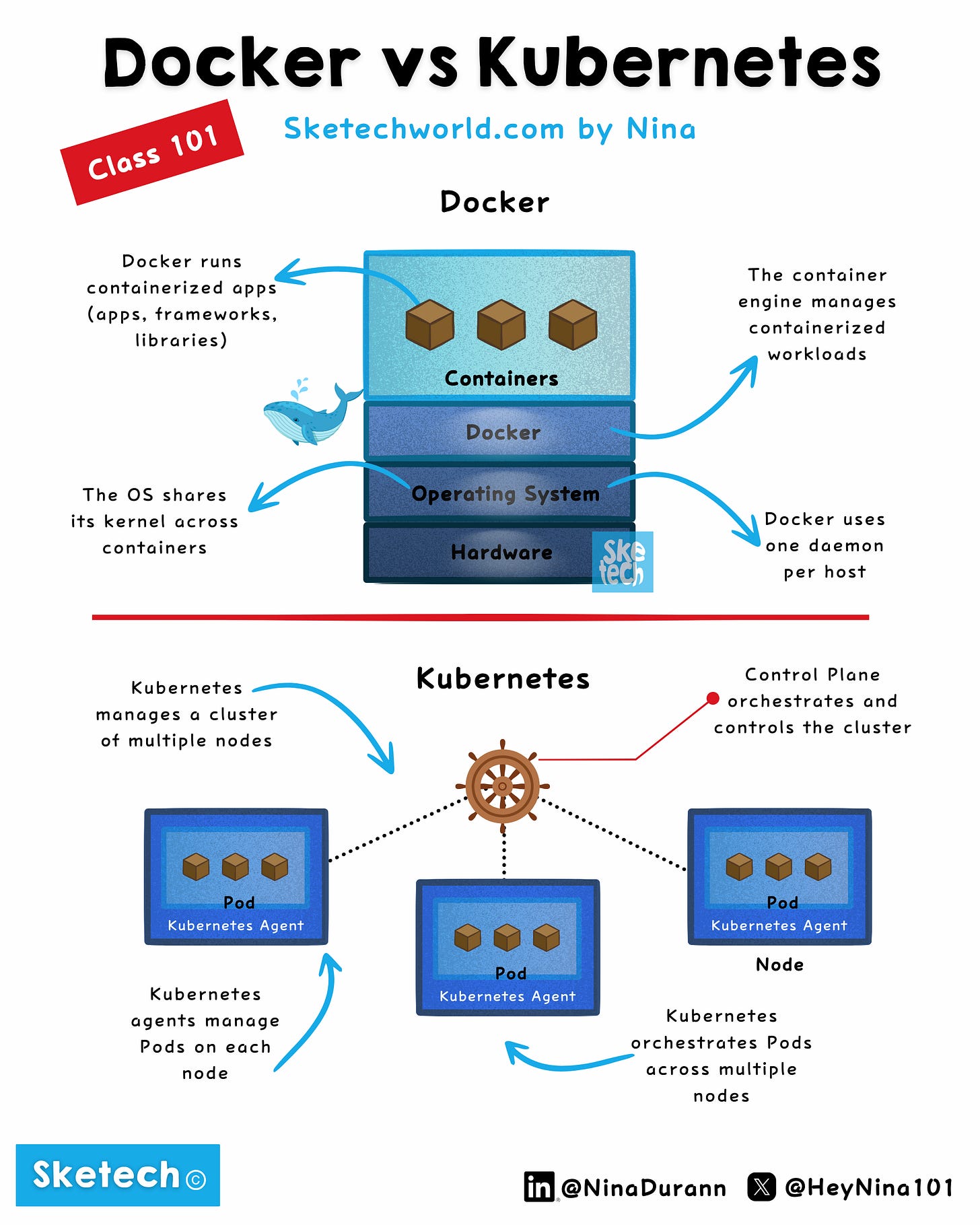
1. Docker: The Foundation of Containerization
Solves the "it works on my machine" problem by packaging applications and dependencies into lightweight, portable containers.
Key Features
Creates container images from a Dockerfile.
Defines filesystem layers, dependencies, and commands in the Dockerfile.
Ensures consistency across environments (local, testing, production).
Tools: Docker Compose: Manages multi-container applications on a single host.
Use Case: Ideal for building, running, and testing containers in development and CI/CD pipelines.
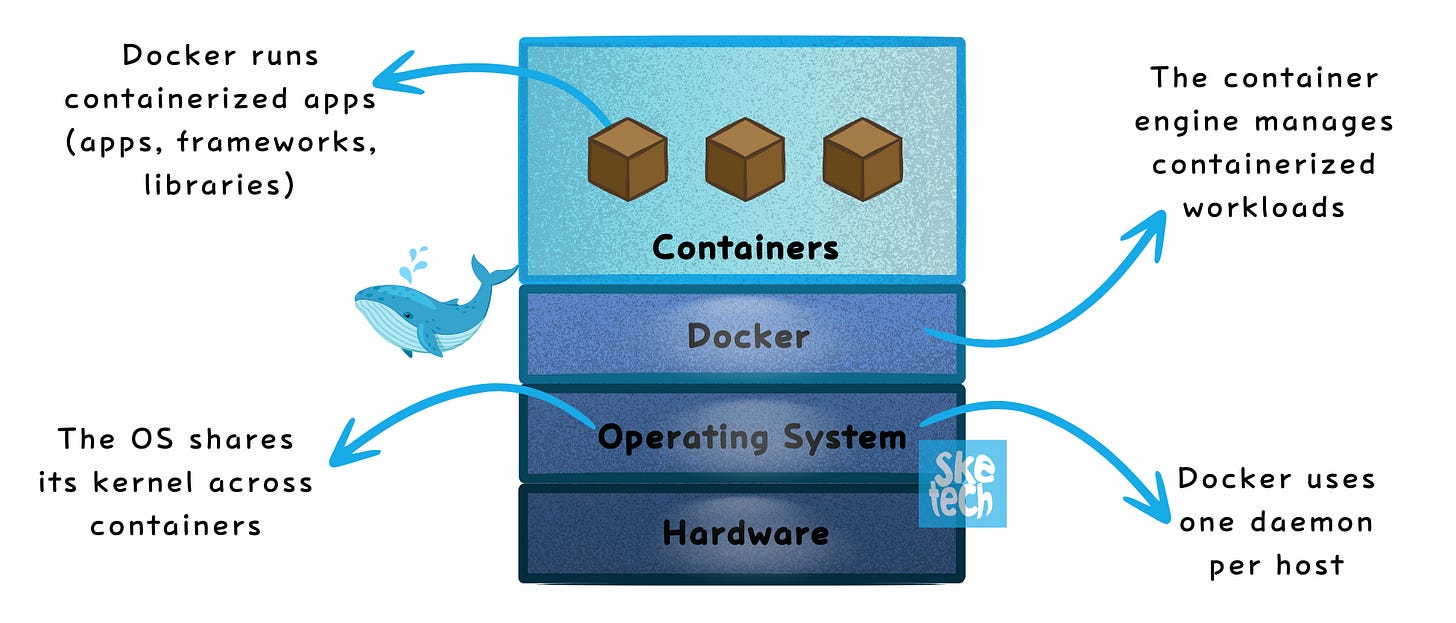
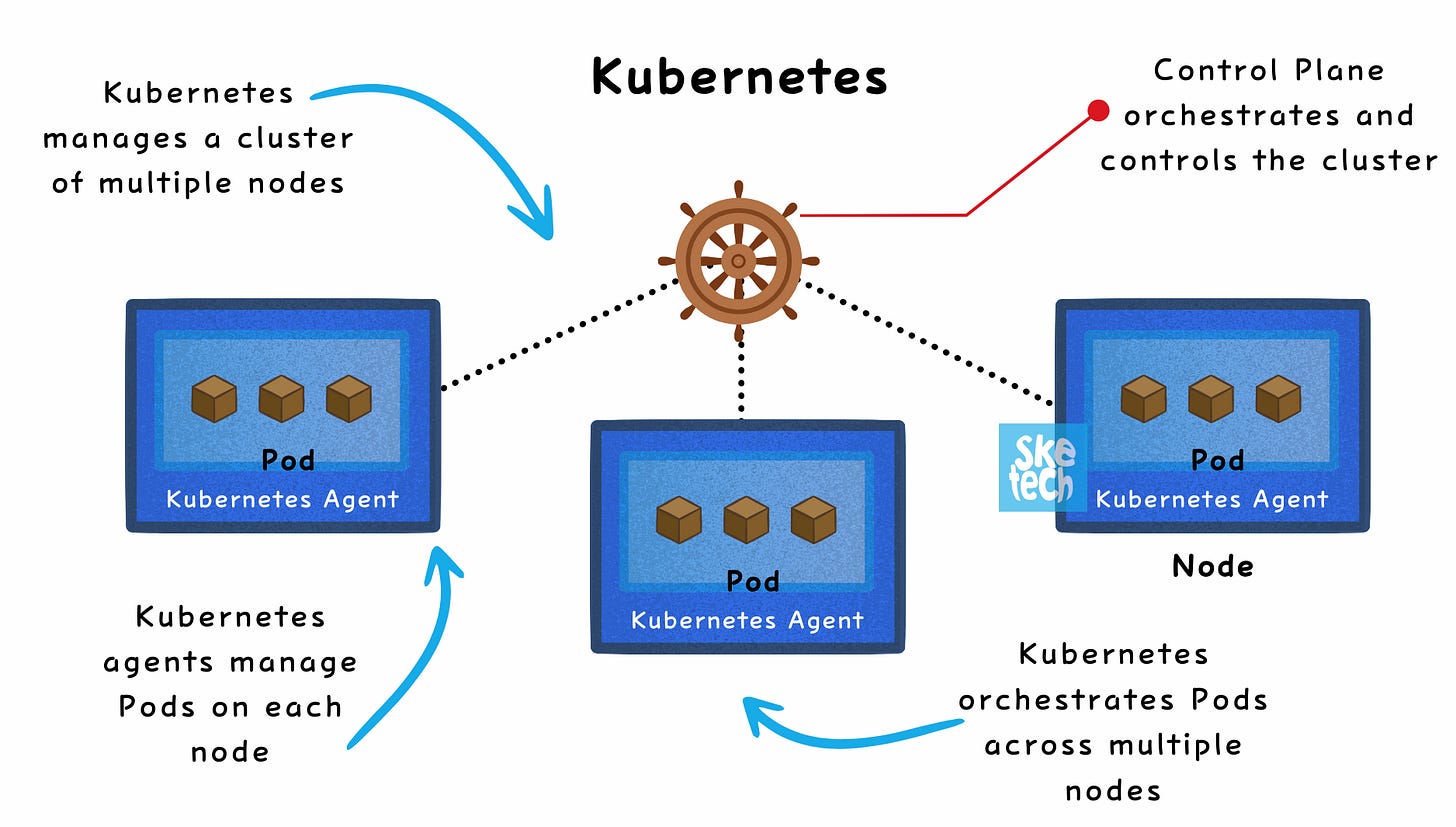
2. Kubernetes: Orchestration at Scale
Manages containerized applications across clusters, enabling scalability, resilience, and automation.
Key Features
Distributes workloads across multiple nodes (unlike Docker, which operates on a single host).
Automates deployments, scaling, and networking.
Horizontal Scaling: Uses Horizontal Pod Autoscaler (HPA) to adjust resources based on demand.
Networking: Manages communication through Services and Ingress.
Self-Healing: Monitors and restarts failed pods to maintain application health.
Core Concepts
Pod: The smallest deployable unit, which can contain one or more containers.
Desired State: Defined in YAML files, ensuring the system always matches the declared configuration.
Configurations: Managed using ConfigMaps and Secrets.
Service Discovery: Automatically detects and connects services within the cluster.
Use Case: Essential for running production-grade, scalable, and resilient containerized applications.
3. How They Work Together
Docker builds and runs containers, while Kubernetes orchestrates them at scale.
🪝For example, in a typical workflow, Docker is used in CI/CD pipelines to create container images, which are then deployed to a Kubernetes cluster for production. Tools like Helm and ArgoCD can further optimize this process, automating deployments and managing complex configurations.
4. Do You Need Both?
If you’re running a handful of containers, Docker alone might suffice. But if you need high availability, auto-scaling, and self-healing, Kubernetes is the next step. Together, these tools are key to mastering containerization in the cloud-native era.
5. Here 10 Points to Clear the Confusion!
Docker
A containerization platform.
Packages applications and dependencies into containers.
Ensures portability across environments.
Runs containers on a single host.
Used in CI/CD pipelines for deployment automation.
Kubernetes
A container orchestration system.
Manages containerized applications at scale.
Handles deployment, scaling, and networking.
Distributes workloads across multiple nodes.
Optimized for microservices and cloud-native applications.
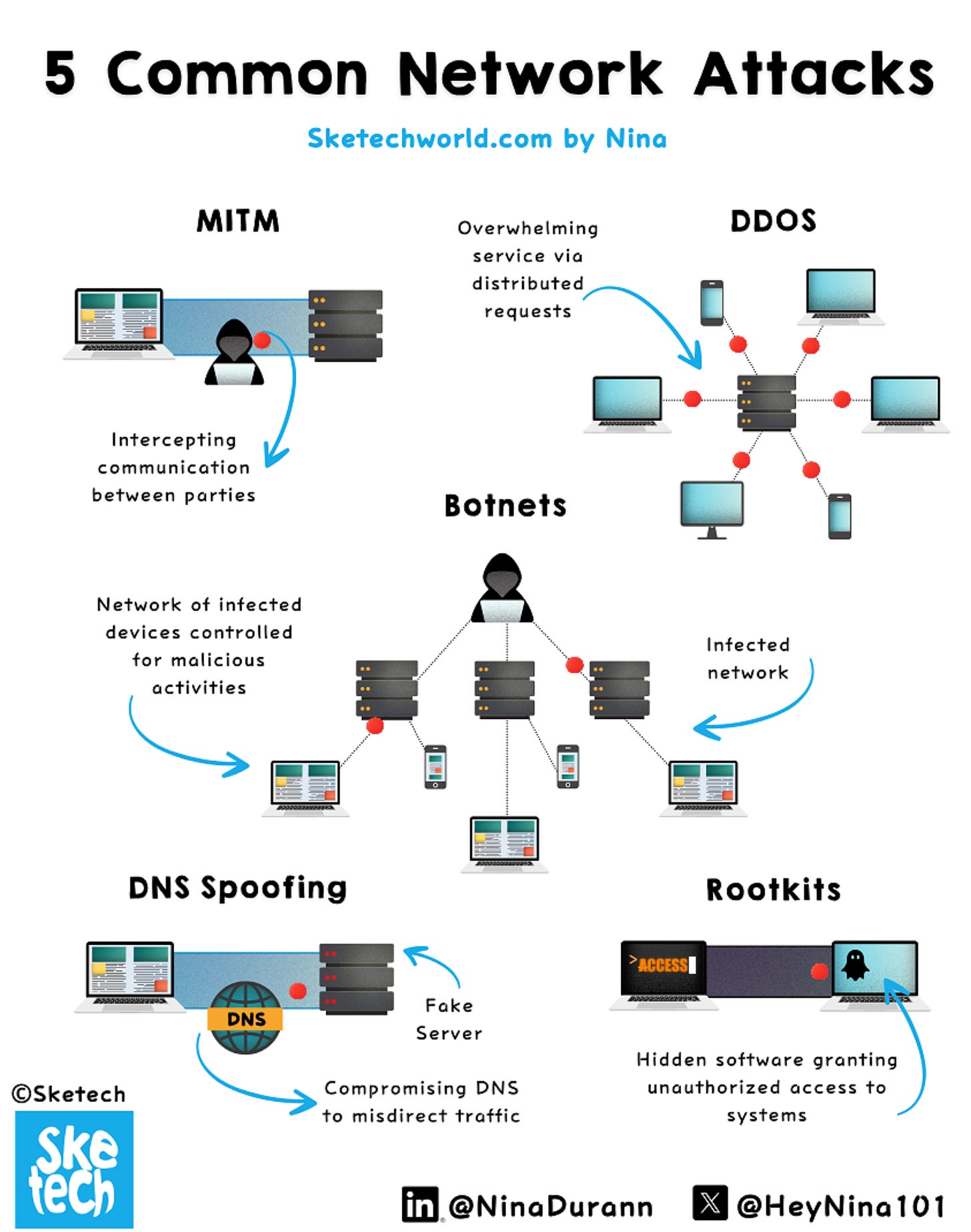
5 Common Network Attacks Explained
Every network attack exploits trust or weaknesses in systems. Recognizing their patterns is the first step to prevention. Here’s how five common attacks operate and why they matter.
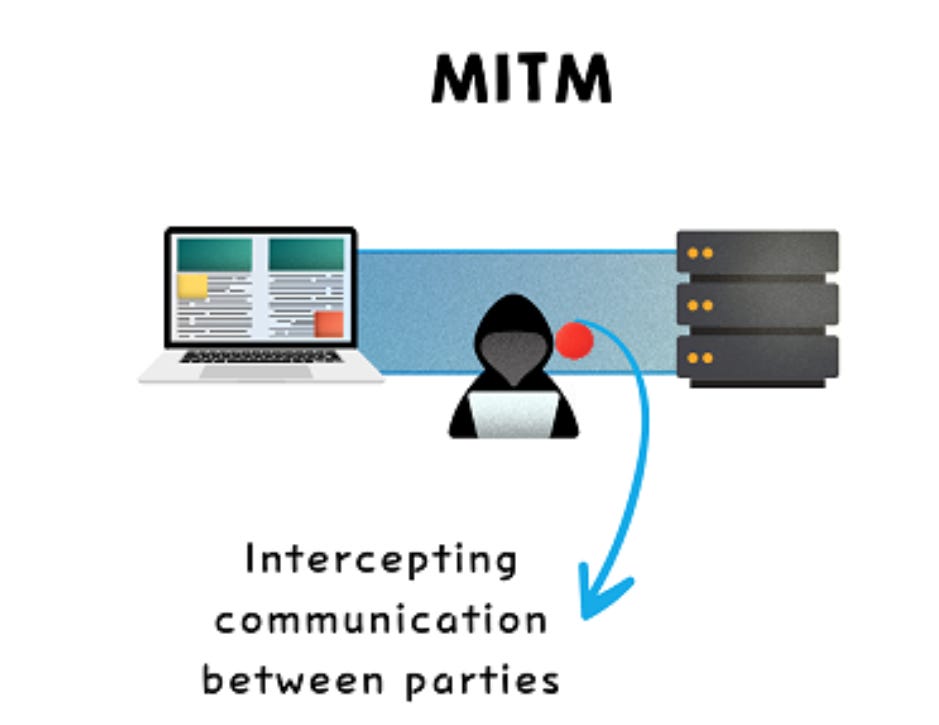
1. MITM (Man-in-the-Middle)
Attacker intercepts communication between two parties.
Used to steal sensitive data like login credentials.
Common in unsecured networks like public Wi-Fi.
Exploits weak encryption or unencrypted communication.
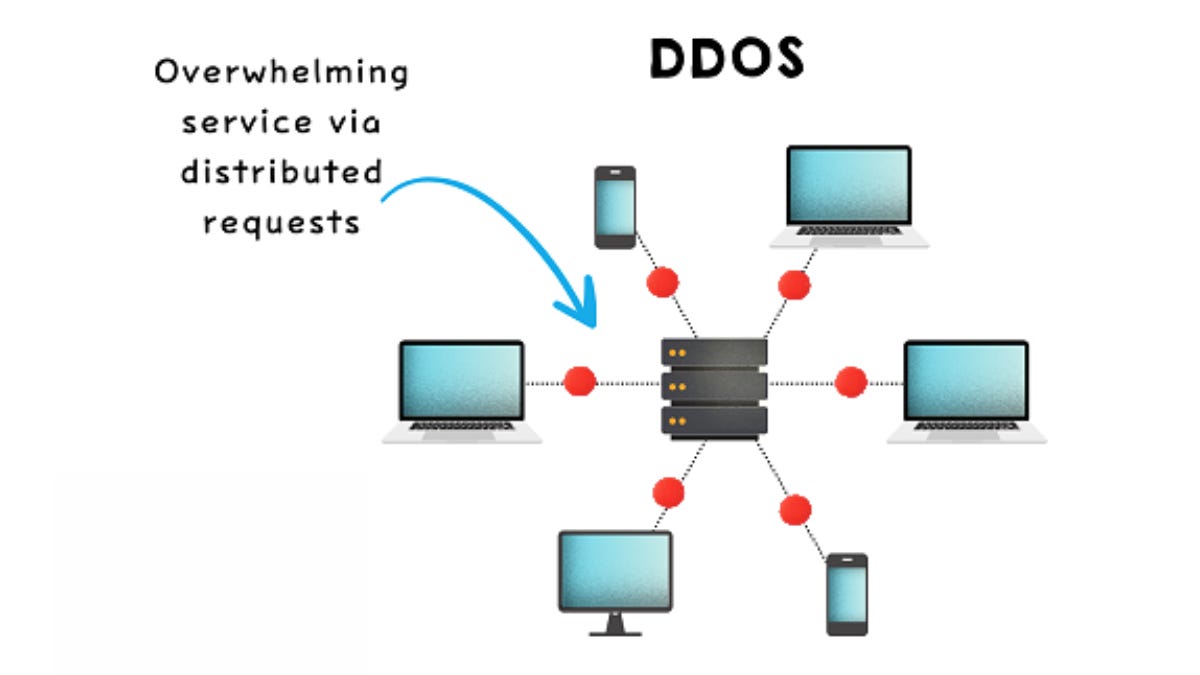
2. DDOS (Distributed Denial of Service)
Overloads servers with massive traffic from multiple sources.
Causes service unavailability for legitimate users.
Often involves botnets to amplify the attack.
Targets websites, servers, or online applications.
3. Botnets
Network of infected devices controlled by a hacker.
Used for large-scale attacks, including DDOS.
Operates silently, often without the user’s knowledge.
Devices include PCs, servers, IoT gadgets.
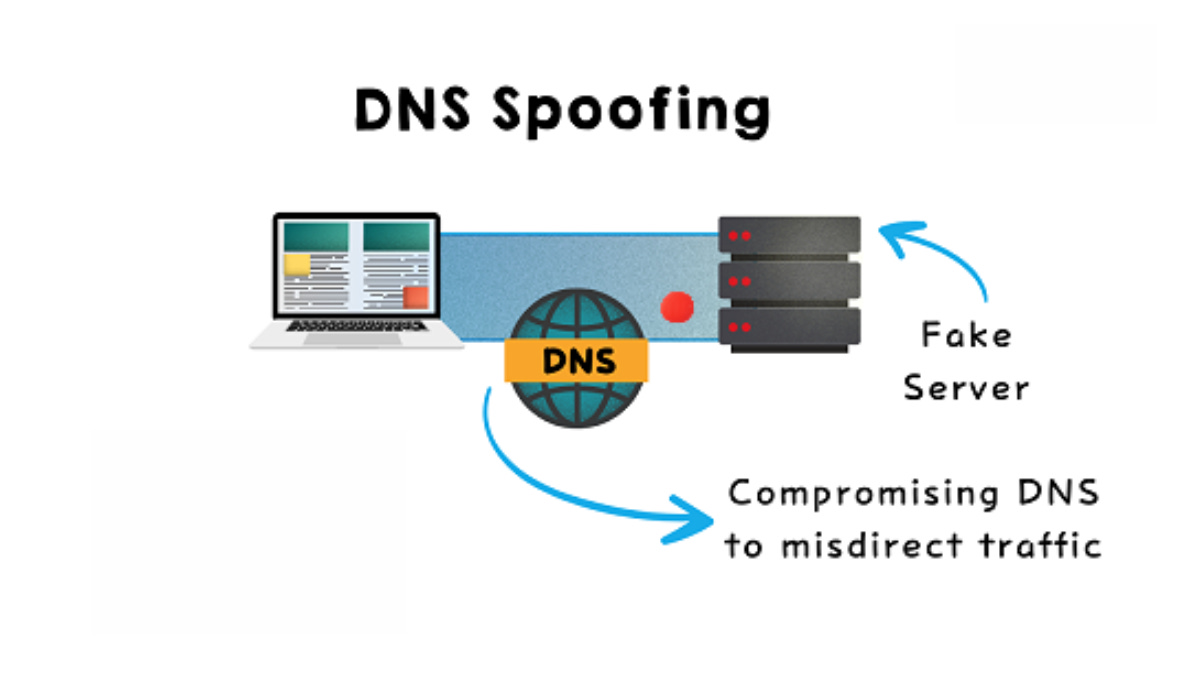
4. DNS Spoofing
Alters DNS records to redirect traffic to fake websites.
Exploited for phishing or malware distribution.
Victims unknowingly visit malicious sites.
Compromises DNS servers or uses cache poisoning.
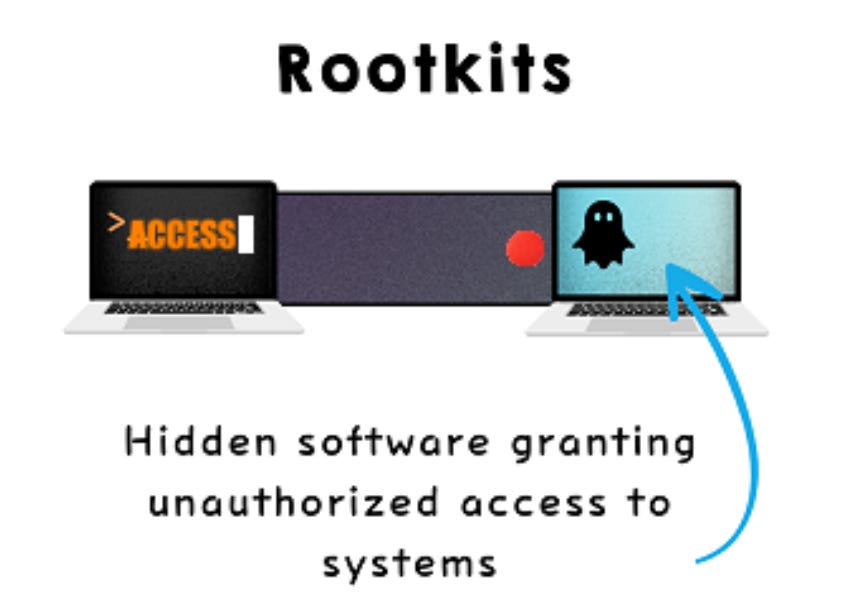
5. Rootkits
Hidden software granting unauthorized system access.
Operates stealthily, avoiding detection by antivirus tools.
Modifies system files or processes.
Often used for long-term data theft or control.
Keep your systems updated and secure to avoid these threats.
Complete Visual Breakdown 👇
A huge thank you to everyone 🤗!
This week, we’ve welcomed 152 new readers, and I’m so grateful to have you on this journey!
If these visuals made your day easier or added value to your work, a heart ♥️ would mean a lot to me. Let’s keep building this together!
Enjoy your weekend, and I’ll catch you in the next edition!
Nina
Sketech Newsletter
Crafted to make software concepts unforgettableMore Articles You’ll Love!
Drop a ❤️- it means a lot!